Nvidia has issued an update to fix a quintet of severe vulnerabilities affecting its GPU display drivers. Just ahead of the weekend the Green Team published a security bulletin about the serious issues, "that may lead to local code execution, denial of service, or escalation of privileges". In brief you can grab an update here, but can take some solace that all of the vulnerabilities require local machine access to exploit.
Of the five vulnerabilities, on Windows systems using an Nvidia GPU driver, three are judged to be high severity and two medium. I've reproduced the threat details and level table beow, with links to the CVE entries below:
|
CVE |
Description |
Base Score |
|
NVIDIA Windows GPU Display Driver contains a vulnerability in the user mode video driver trace logger component. When an attacker has access to the system and creates a hard link, the software does not check for hard link attacks. This behavior may lead to code execution, denial of service, or escalation of privileges. |
8.8 |
|
|
NVIDIA Windows GPU Display Driver contains a vulnerability in DirectX drivers, in which a specially crafted shader can cause an out of bounds access of an input texture array, which may lead to denial of service or code execution. |
7.8 |
|
|
NVIDIA Windows GPU Display Driver contains a vulnerability in DirectX drivers, in which a specially crafted shader can cause an out of bounds access to a shader local temporary array, which may lead to denial of service or code execution. |
7.8 |
|
|
NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape in which the software uses an API function or data structure in a way that relies on properties that are not always guaranteed to be valid, which may lead to denial of service. |
5.6 |
|
|
NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape in which an incorrect use of default permissions for an object exposes it to an unintended actor, which may lead to information disclosure or denial of service. |
5.2 |
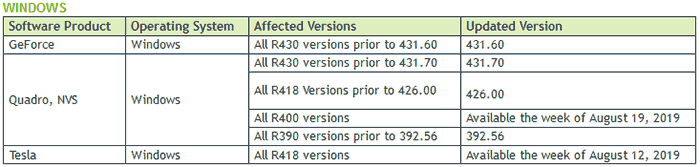
To be clear, this security bulletin goes beyond the consumer GeForce series GPU drivers for Windows. The same vulnerabilities are present in Quadro, NVS and Tesla drivers on Windows systems. Please check the table below for the particular updated driver version you should be looking for. You will see some fixed GPU drivers are still being worked upon.
On a positive note, if you are using a GeForce GPU and haven't yet updated to the latest driver, you will be getting optimisations for Wolfenstein: Youngblood and Cyberpilot, support for a trio of new G-Sync Compatible Displays, and v431.60 WHQL adds support for the GeForce RTX 2080 Super.













