Earlier this week Intel released details about a vulnerability in its integrated graphics hardware. Its advisory ID was INTEL-SA-00314 and it talked about the CVE-2019-14615 vulnerability. Products from 3rd Gen Core up to 10th Gen are affected including the contemporaneous Xeon, Pentium, Celeron and Atom products. Intel was made aware of this vulnerability as far back as August so already has patches available and links to recommended new drivers for both Windows and Linux users (scroll down this page about half way).
All so regular and nothing surprising so far… However, since the updated drivers have been released, Linux-centric tech site Phoronix has been busy checking and testing the new drivers (on Linux of course) to see if there are any performance penalties, or other aberrations, delivered with the vulnerability patches.
Intel describes the CVE-2019-14615 vulnerability as follows: "Insufficient control flow in certain data structures for some Intel Processors with Intel Processor Graphics may allow an unauthenticated user to potentially enable information disclosure via local access." Please note the key phrase - local access - but Phoronix thinks that WebGL within web browsers is another possible attack vector.
In its Linux testing, Phoronix was initially unperturbed by results on processors sporting Intel Gen9 graphics. With this hardware the mitigation clears all execution unit (EU) states at each context switch - and the observed performance impacts were minimal. Moving on to how the patch affects Intel Gen7/Gen7.5 graphics - the story changes dramatically.
Phoronix notes that the Gen7 graphics mitigation "is much larger across two patches and relies upon a custom EU kernel being called prior to every context restore for clearing EU and URB resources." Getting down to brass tacks, the security patch "obliterates Gen7 iGPU performance," opines the source, going on to say that iGPU performance on Ivy Bridge and Haswell is "completely wreck[ed]".
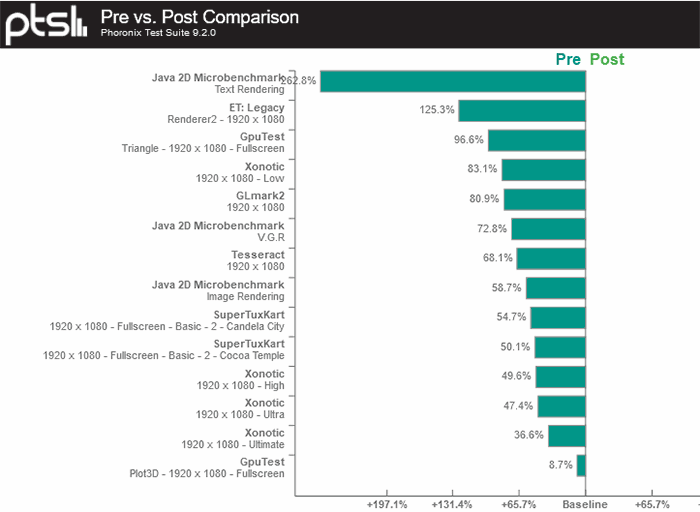
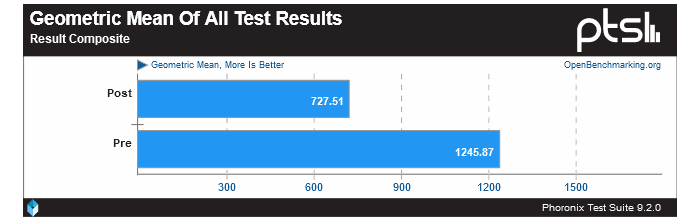
Above you can see a disastrous showing for the post-patch Haswell Core i7 4790K system relying on its iGPU, and Phoronix provides a mean of all tests from its own custom suite, as in the image embedded below. The overall result shows that the patched system is about 42 per cent slower in a wide selection of graphics benchmarks.
The source comments that Haswell seems to be hit particularly hard by the vulnerability patches. Intel Core i7 3770K Ivy Bridge iGPU graphics are reduced in the same test suite by 18 per cent. It is noted that the current Intel graphics driver patches do not respond to the generic 'mitigations=off' kernel parameter. With the time Intel has already had to sink into its driver patches the hope that Haswell/Ivy Bridge performance will be improved in drievr updates is slight.
Moving on to Windows OS users, in its patch notes Intel says that "Platforms based on Ivy Bridge, Bay Trail and Haswell do not have full mitigations at this time for the Windows OS. Updating the drivers for these platforms per the recommendation below will substantively reduce the potential attack surface." So, there is hope that newer better patches will come along after further development and validation.
If anyone relies on a Haswell iGPU for some aspect of their day to day computing and would like to run a couple of before - then after - GPU performance tests on Windows please feel free to share your findings in the comments section below.














