Back in mid March we first heard about four classes of security vulnerabilities affecting AMD processors, from a security outfit called CTS Labs. We were told that “13 serious flaws,” subdivided into Masterkey, Ryzenfall, Fallout, and Chimera classes, could be utilised by hackers: to take control over Ryzen and Epyc systems, to infect the systems with malware, steal credentials, and even physically damage the hardware. However, as the dust settled, it became clear that most of the vulnerabilities required local admin access, and that CTS Labs might have had ulterior motives for its revelations.
Initially AMD responded by saying that CTS Labs was unknown to them and that it was unusual for a security firm to publicise such vulnerabilities without first reaching out to the company affected. Later there was much speculation about whether CTS might have been motivated to abruptly and sensationally reveal ‘AMD processor flaws’ for the purpose of stock price manipulation.

Now we have some updates on what is happening with regards to the CTS Labs vulnerabilities discovered in AMD processors, thanks to some digging by Tom’s Hardware. Earlier in the week the tech site was contacted by CTS Labs saying it was concerned about the lack of updates from AMD regarding the vulnerabilities. CTS went on to say that it thought the various categories of vulnerabilities would take months to fix, with some, like Chimera, requiring hardware changes.
AMD was contacted by Tom’s Hardware directly to check on progress. An answer came back as follows: “Within approximately 30 days of being notified by CTS Labs, AMD released patches to our ecosystem partners mitigating all of the CTS identified vulnerabilities on our Epyc platform as well as patches mitigating Chimera across all AMD platforms.” In addition AMD noted that the patches were in the final testing phase with ecosystem partners ahead of public distribution.
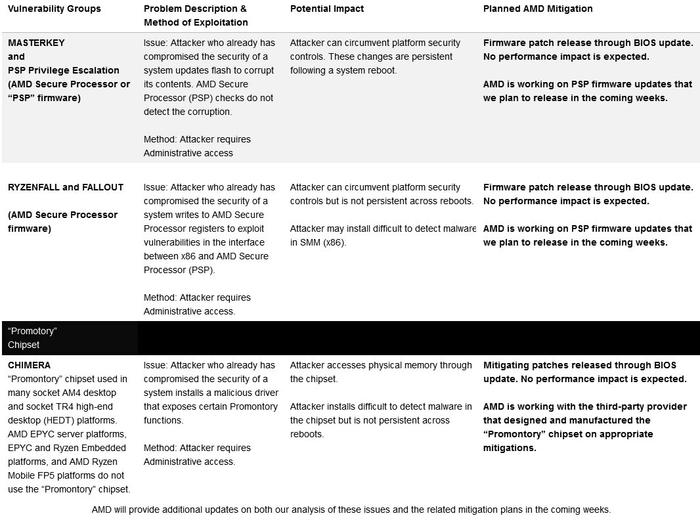
Overall it is good to hear that AMD is confident that all the CTS Labs vulnerabilities are mitigated by patches supplied to partners. Furthermore, in an update provided by AMD CTO and SVP of Technology and Engineering, Mark Papermaster, about a week after the initial revelations, it was asserted that software and firmware patches would result in no expected performance impacts.













