About a week ago cyber-security research firm and consultancy, CTS Labs, published various materials concerning multiple critical security vulnerabilities in AMD's 'Zen' core processor family. There followed quite some controversy over the way in which these alleged vulnerabilities were publicised, and about how practical it would be for these vulnerabilities to be exploited in the wild.
One of the CTS Labs news graphics published last week.
AMD had only 24 hours notice of the CTS security vulnerability research so its initial response was understandably brief - mainly promising an immediate investigation and updates to keep customers informed about findings and possible actions. Yesterday evening AMD CTO and SVP of Technology and Engineering, Mark Papermaster, delivered his measured response - covering AMD's own technical assessment of the issues and planned mitigation actions.
First of all Papermaster made it clear that the CTS Labs findings were nothing to do with the AMD 'Zen' CPU architecture or the Google Project Zero exploits made public on 3rd Jan, 2018. Instead these were seen to be issues in "the firmware managing the embedded security control processor in some of our products (AMD Secure Processor) and the chipset used in some socket AM4 and socket TR4 desktop platforms supporting AMD processors".
As I noted in the initial HEXUS report, Papermaster emphasised that the CTS Labs security issues "require administrative access to the system, a type of access that effectively grants the user unrestricted access to the system and the right to delete, create or modify any of the folders or files on the computer, as well as change any settings." If an attacker already had this level of access, said Papermaster, there would be plenty of other attacks at their disposal, too.
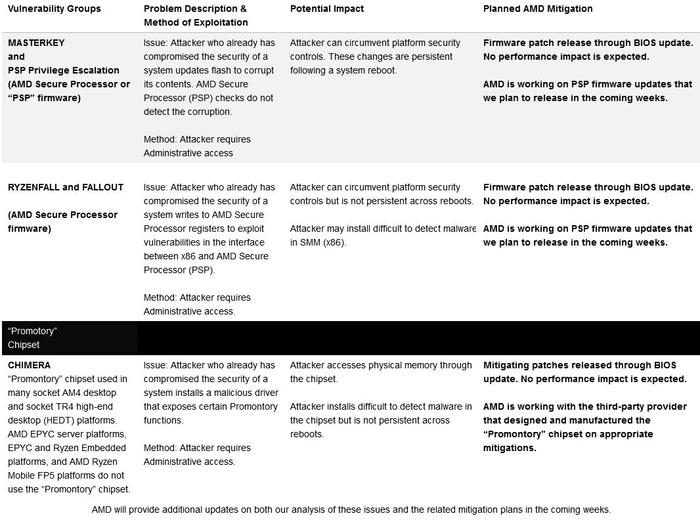
click to zoom in
As you can see above, AMD seems to already have its game plan spelled out very clearly. With all of the vulnerability classes it expects that updates/fixes will have no impact on the host system performance. Most of the updates are scheduled for "the coming weeks" either through the BIOS or other means. Since AM4 isn't very old, third parties supporting the platform should be very willing to issue BIOS updates and so on.
CTS proof of concept video for Masterkey 1 exploit, from yesterday
Update: 22/03/18 14:00
HEXUS has since been contacted by a representative of CTS who has unequivocally stated that, as we mistakenly alluded to in the original piece, 'Viceroy is absolutely NOT a client of CTS and both CTS and Viceroy have publicly stated that.' We apologise for this error.