Apple Mac computers were targeted for the first time by ransomware this weekend, reports Reuters. Researchers at Palo Alto Networks Inc observed the first thrust of this particularly nasty brand of malware in the wild.
Ransomware seeks to infect systems, encrypt user files, then get the user to pay up for a decryption key to get their files, or even access to their system, back. It is estimated that cyber criminals extract ransoms of "hundreds of millions of dollars a year", from their victims which had until now been typically been Windows users. Looking around it seems that ransomware attacks are a very clear and present threat to Android users too.
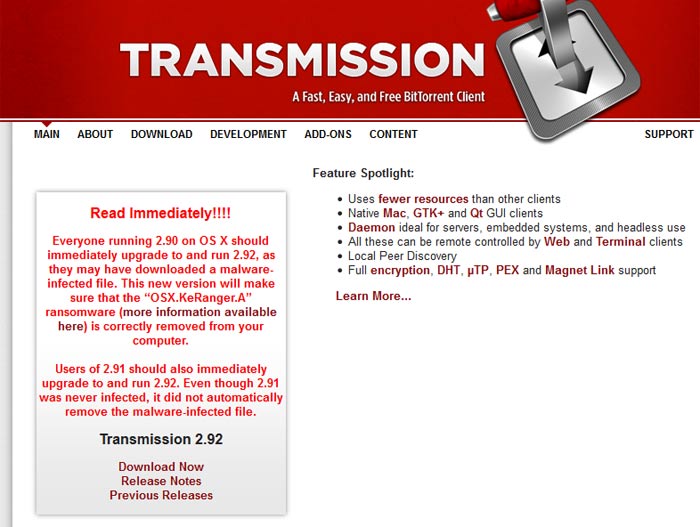
'KeRanger' ransomware was delivered to Mac users via an infected version of the Transmission open source BitTorrent peer-to-peer file sharing client. Palo Alto Threat Intelligence Director Ryan Olson said the infected software propagation began on Friday when Transmission 2.9 was released. Worryingly, the malware authors managed to get their code in the official release of this program, downloadable from the official site. In a telephone interview with Reuters, Olson said "This is the first one in the wild that is definitely functional, encrypts your files and seeks a ransom".
It is interesting to note that "The KeRanger application was signed with a valid Mac app development certificate; therefore, it was able to bypass Apple's Gatekeeper protection". Apple has been notified of the treat and has since revoked the abused certificate and updated the XProtect antivirus signature.
Act now if you are a Transmission user
The program has since been updated and a new version released with a patch that automatically removes the ransomware from infected Macs. If you have any suspicion that you downloaded or updated Transmission on Friday or Saturday it is advised that you install the update, version 2.92, as soon as possible. You probably still have time to do so as "KeRanger is programmed to stay quiet for three days after infecting a computer, then connect to the attacker's server and start encrypting files so they cannot be accessed".
To decrypt your files KeRanger asks for 1 bitcoin (approx US$400) to be transferred.













