The CERT Coordination Centre (CERT/CC) at Carnegie Mellon University has found a flaw in antivirus firm AVG's Secure Search toolbar which could allow hackers to remotely attack and execute malicious code.The researchers have issued a warning for AVG anti-virus software suite users as a hole in one of the components within the toolbar was discovered. The fault exists in an Active X control called ScriptHelperApi in Internet Explorer, as provided by AVG Secure Search, which exposes sensitive data to websites.
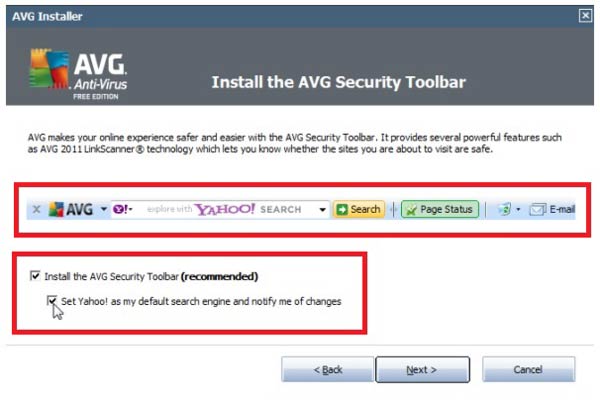
Versions 18.1.6 and older of AVG Secure Search and AVG SafeGuard allow websites to invoke ScripHelperApi. As a result, the remote-code-execution flaw could allow an attacker to install and run malware, or collect personal data on an affected computer.
"This control does not internally enforce any restrictions on which sites may invoke its methods, such as by using the SiteLock template," said Will Dormann, a vulnerability analyst at CERT/CC, in a security advisory. "This means that any website can invoke the methods exposed by the ScriptHelper ActiveX control."
The security add-on toolbar was bundled with various software downloads and installers and usually installs itself on top of the Internet Explorer UI without users intentionally downloading the service, and has thus been dubbed as "foistware". It bypasses the security feature which asks users for confirmation before executing ActiveX controls, and automatically places itself on a list of pre-approved ActiveX controls in the browser's system registry. Additionally, it is also excluded from IE's Protected Mode.
"The installer for AVG Secure Search also sets the ElevationPolicy registry value for the control, which means that the control is excluded from the Internet Explorer Protected Mode sandbox. The installer for AVG Secure Search sets the Preapproved registry value, which bypasses the Internet Explorer ActiveX Opt-In feature that was introduced with IE 7," explained Dormann.
If a user opens a specially designed HTML Web page, email or attachment in IE, the rogue code would be executed with the privileges of the logged-in user, and thus allow attackers to take over the user's computer. The exploit only affects versions of the toolbar configured for IE7 and above, and AVG has deployed a hotfix for the issue in AVG Secure Search toolbar version 18.1.7.598 and AVG Safeguard 18.1.7.644, until it finds a more permanent solution.
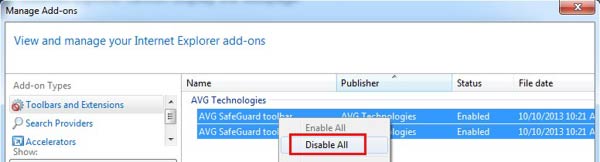
Users can also disable the AVG ScripHelper ActiveX control in IE's settings to resolve the problem. However, there is no evidence showing that this error has been exploited maliciously so far.













