Researchers have managed to create a computer virus which builds itself from pieces of code that are commonly present on many computers. By utilising common and benign code to assemble its malignant self the malware should be able to avoid detection by conventional anti-virus programs. The team from the University of Texas say they have created an electronic version of Frankenstein’s monster.
An abstract from the new research paper from Texas University researchers Vishwath Mohan and Kevin Hamlen summarises the project aims and scope;
“This paper proposes a new self-camouflaging malware propagation system, Frankenstein, that overcomes shortcomings in the current generation of metamorphic malware. Specifically, although mutants produced by current state-of-the-art metamorphic engines are diverse, they still contain many characteristic binary features that reliably distinguish them from benign software.
Frankenstein forgoes the concept of a metamorphic engine and instead creates mutants by stitching together instructions from non-malicious programs that have been classified as benign by local defenses. This makes it more difficult for feature-based malware detectors to reliably use those byte sequences as a signature to detect the malware. The instruction sequence harvesting process leverages recent advances in gadget discovery for return-oriented programming. Preliminary tests show that mining just a few local programs is sufficient to provide enough gadgets to implement arbitrary functionality.”
The research was part funded by the US Air Force and presented at the USENIX Workshop on Offensive Technologies in Washington earlier this month. Kevin Hamlen, one of the researchers, said that Frankenstein could be useful to infiltrate enemy computer systems with unknown antivirus defences. The malware, once into the enemy system, could assemble itself from existing files on the target computer that would “help it blend in with the crowd”, he said. The Frankenstein malware would be especially invisible to virus detection systems using signature whitelisting.
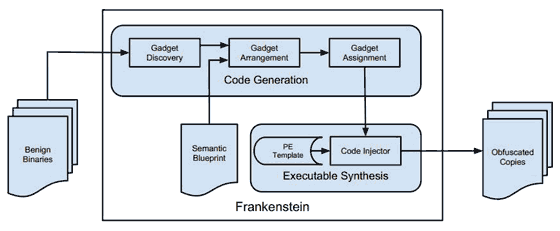
The code created by the researchers was just a proof of concept and used to run a couple of harmless algorithms on the target machine. Scientists who create malware like this often use their findings to help anti-virus vendors and legitimate software firms find ways to fix or detect these new types of threats before criminals get to work using the same technology.
The New Scientist says Microsoft has released an updated version of EMET (24th July 2012) which “features a new defence designed to stop malware from executing other software's code, just as Frankenstein does. It works by wrapping key software in a layer of code that checks whether parts of the software are being repurposed.” In this ongoing game of malware/anti-malware leapfrog Microsoft’s protections have already been bypassed by an Iranian security researcher. “I did patched EMET to be deactivated completely. BOOM!” claimed Shahriyar Jalayeri on his blog.













