Cloudflare is a service that protects many big name websites from “all manner of attacks” while providing optimal performance in web page serving. Key to its business are security, reliability and performance. The firm is impressive in its stature, serving more web traffic that Twitter, Amazon, Apple, Instagram, Bing, and Wikipedia combined and engaging with 10,000 new customers a day via its 118 data centres worldwide.
With the above responsibility in mind you won’t be surprised to hear that Cloudflare has put a lot of work into making sure its cryptography is top notch. What might be surprising is the way Cloudflare generates its random numbers that are both unpredictable and kept secret from any adversary – it uses LavaRand (via HardOCP).

Interestingly, LavaRand is on display for anyone who passes through the Cloudflare lobby at its HQ in San Francisco (pictured above). Despite being at the core of its random number generation LavaRand isn’t hidden away in some vault. Cloudflare uses images of the state of the wall of lava lamps as an additional source of entropy (like chaos, disorder or randomness) for its production machines generating keys to encrypt web traffic. Put simply, the images from the live video stream are turned into a “stream of random, unpredictable bytes”.
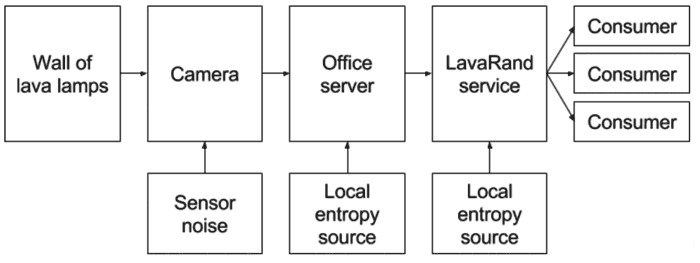
Cloudflare has analysed possible threats to LavaRand, such as someone using their own camera to monitor the lamps, someone turning off all the lamps, and so on, but with all the other entropy sources in the Cloudflare system the only ‘fatal’ attack would be one where the attacker runs code on the production service which produces the final entropy feed. In summary, Cloudflare says that LavaRand is probably not necessary, due to the existing randomness sources in production, but it is there for visual office flair and a final hedge making Cloudflare even harder to hack.













