A computer chip dubbed Morpheus has weathered a storm of 500+ hackers over three months, with tens of thousands of dollars from DARPA at stake. Morpheus was designed by a team at the University of Michigan as an 'unhackable' chip and has, so far lived up to its billing.

The U-M blog says Todd Austin was the team’s leader – he is the university's S. Jack Hu Collegiate Professor of Computer Science and Engineering. Trying to describe the chip's hack-proofing strategy in layman's terms Austin asks us to "Imagine trying to solve a Rubik’s Cube that rearranges itself every time you blink. That’s what hackers are up against with Morpheus," he asserted. "It makes the computer an unsolvable puzzle".
Delving deeper into the actual workings of Morpheus, the major principles at play in making it 'unhackable' is how it leverages hack detection plus "encryption and churn". The U-M blog says that "Encryption randomizes the important undefined semantics that hackers need to launch a successful attack, while churn re-randomizes them while the system is running. This puts attackers in a race against the clock to discover the information that they need." Unfortunately for would-be hackers, the churn rate spikes if it detects hack attempts via undefined semantics, so there is little chance of building up to a working hack.
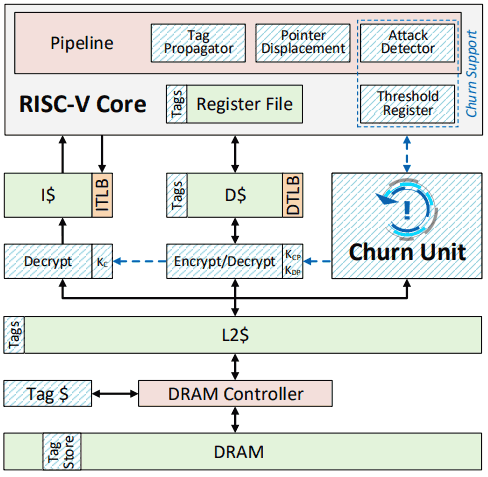
Importantly, Morpheus' security acrobatics are said to be "transparent to software developers and end users," and in the DARPA sponsored bug bounty hackathon it was used as a processor for a mock medical database.
If you want to learn more about Morpheus its architecture is detailed in a 2019 paper titled Morpheus: A Vulnerability-Tolerant Secure Architecture Based on Ensembles of Moving Target Defences with Churn.













