Intel quietly updated its microcode update guidance (PDF) on 2nd April. The last time we checked this document, back in mid-March, it was good news and Intel simultaneously revealed via a blog post that it had updated the microcode for all of the products it had launched in the past five years. The latest update to the PDF isn't very good news, as if you check through the document you will see that many processors/chipsets have been shifted to a new production status labelled 'stopped'.
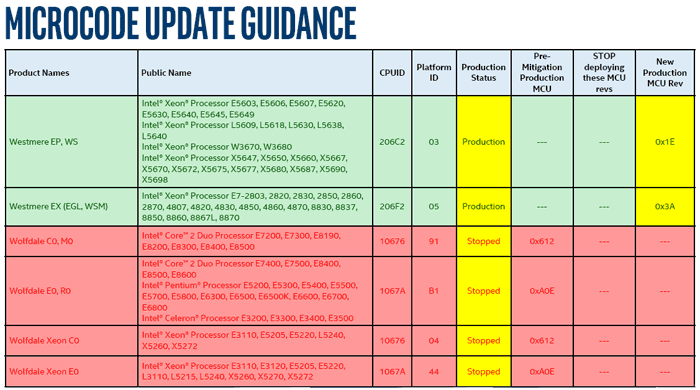
An example of the range of new 'stopped' production status notices is given above. You can see clearly that Intel has put a halt to producing microcode updates for its entire Wolfdale line. (I used to run one of these CPUs) These 45nm processors were first released as far back as Q1 2008.
In all, as The Register reports, there are over 230 processors that have had their production status 'stopped'. In its inimitable way the Reg says that the 10 product families will be neglected by Intel fixers and patchers "in some cases because it's too tricky to remove the Spectre v2 class of vulnerabilities". As well as Wolfdale processors, you will find that Spectre and Meltdown patch development statuses for Bloomfield, Bloomfield Xeon, Clarksfield, Gulftown, Harpertown Xeon C0 and E0, Jasper Forest, Penryn/QC, SoFIA 3GR, Wolfdale Xeon, Yorkfield, and Yorkfield Xeon families have all been shunted to 'stopped'.
The official microcode update guidance document includes some explanation for the 'stopped' status just behind the cover page. It says that "after a comprehensive investigation of the microarchitectures and microcode capabilities for these products, Intel has determined to not release microcode updates for these products for one or more reasons". The reasons, three of them in total, are reproduced below:
- Micro-architectural characteristics that preclude a practical implementation of features mitigating Variant 2 (CVE-2017-5715)
- Limited Commercially Available System Software support
- Based on customer inputs, most of these products are implemented as 'closed systems' and therefore are expected to have a lower likelihood of exposure to these vulnerabilities.
We don't know which respective processor families are impacted by which of the above bullet points.
Some good news
Elsewhere in the document there is good news for users of processors in the Arrandale, Clarkdale, Lynnfield, Nehalem, and Westmere families. Intel now has working fixes for these in production, according to the status table. "We've now completed release of microcode updates for Intel microprocessor products launched in the last 9+ years that required protection against the side-channel vulnerabilities discovered by Google Project Zero," an Intel spokesperson told The Reg in a supplementary emailed statement.













