Microsoft has released an emergency security patch for a flaw discovered in its Font Driver software. The patch, which was released a few hours ago outside of Microsoft's usual monthly schedule, will prevent remote code execution by those looking to exploit a critical Microsoft Font Driver flaw. All currently supported versions of Windows are affected and will receive the fix via Windows Update.
If your Windows system remains unpatched and you open "a specially crafted document or visit an untrusted webpage" that contains embedded OpenType fonts your PC security could be compromised via a remote code execution attack. Microsoft says, in Security Bulletin MS15-078, that the weakness in its Font Driver comes from how the Windows Adobe (yes, it's them again) Type Manager Library handles OpenType fonts.
In detailing the consequences of the vulnerability Microsoft says that if left unpatched a document that exploits the Font Driver flaw could be used by an attacker to install programs; view, change, or delete data; or create new accounts with full user rights. At the time of the security patch being issued the vulnerability was public but luckily there was no evidence that any Windows users had fallen victim due to the presence of the flaw.
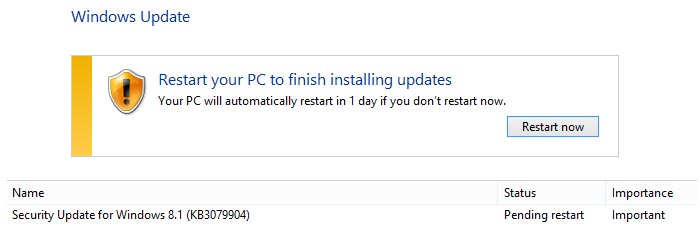
The only way to get the KB3079904 security update is via Windows Update. Please check your Windows Update history to see if it has been installed. If, for some reason, you can't access Windows Update but you think you might be vulnerable to Font Driver flaw exploits Microsoft has detailed some workarounds on the security bulletin page, about two thirds the down.
Security companies FireEye, Trend Micro and experts from Google's Project Zero were credited with discovering the flaw.













