Apple's devices are prey to a zero-click security flaw, which could have been exploitable since February this year or earlier. This is the first time we have seen a vulnerability so severe and that has affected Apple Mac, iPhone, iPad and Watch users alike. There is a very high probability that the zero-day, zero-click exploit was developed by Tel Aviv-based NSO Group, most famous for the Pegasus iPhone surveillance (spyware) software.

Canada's The Citizen Lab is credited with catching out this flaw, reference CVE-2021-30860, in the wild. Citizen Lab researchers were analysing a phone owned by a Saudi activist, a device which was infected with NSO Group's Pegasus spyware, and discovered "a zero-day zero-click exploit against iMessage". The exploit, dubbed 'ForcedEntry' by the researchers, used an attack vector open in Apple's image rendering library – worryingly it is/was effective as an exploit across all Apple's major devices; Apple iOS, MacOS and WatchOS devices.

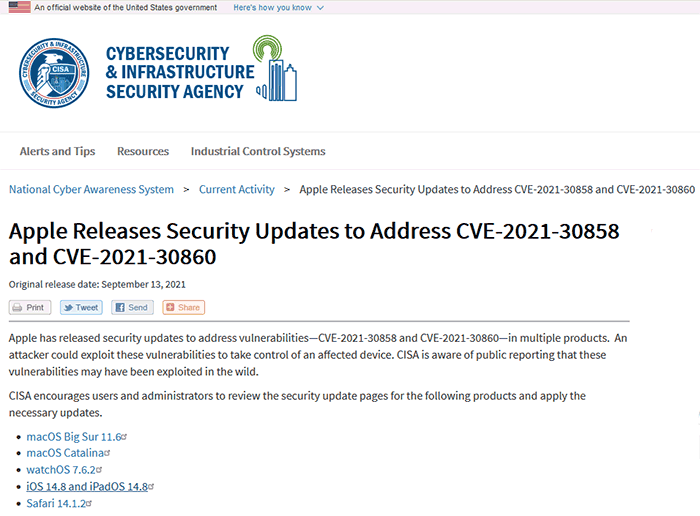
Apple was alerted by The Citizen Lab with regard to its findings on Tuesday, 7th Sept. It has designated the vulnerability as CVE-2021-30860, and on Monday released a short security blog update and has created update fixes for all affected systems. The US Dept of Homeland Security has put together a webpage which links to all the Apple security pages of affected products running MacOS, iOS, WatchOS etc.
The Citizen Lab comments on CVE-2021-30860 being the "latest in a string of zero-click exploits linked to NSO Group". In its conclusions about the discovery of 'ForcedEntry', it criticizes the NSO Group for "Selling technology to governments that will use the technology recklessly in violation of international human rights law". It goes on to make a point that once this "mercenary spyware" tech is being used by such governments it facilitates the spread to other parties, which is characterised as a "harmful marketplace" in need of regulation. The Citizen Lab ends by warning that popular chat apps will likely continue to be "an irresistible soft target," for hackers.
I just updated my iPad Air 2 with the patch (via the built-in update settings), it was 'only' about 350MB but took quite a long time preparing to install and to complete the process. Please be patient and not be tempted to interrupt/restart the update.
Reminder: Apple's California Streaming event is today at 10am PDT (6pm UK time). Expect to see new iPhones unveiled, perhaps more.













