A Windows feature has been uncovered which may be of concern to some but isn't thought to be a 'bug'. Security researcher Barnaby Skeggs was investigating a Windows system file called WaitList.dat which arrived with the release of Windows 8. Not all Windows 8+ PC users will find the file, as it is activated when a user enables the handwriting recognition feature. Once activated, it stores text strings that are input, to help Windows improve prediction, detection and suggestions for handwriting. However, once activated it doesn't restrict itself to saving text strings from your pen input, it also saves keyboard input, and Windows search indexing data.

Last week Skeggs took part in an interview with ZDNet. "In my testing, population of WaitList.dat commences after you begin using handwriting gestures. This 'flicks the switch' (registry key) to turn the text harvester functionality (which generates WaitList.dat) on." Skeggs told ZDNet. As mentioned in the intro, it doesn't restrict itself to data harvesting from your scrawl "Once it is on, text from every document and email which is indexed by the Windows Search Indexer service is stored in WaitList.dat. Not just the files interacted via the touchscreen writing feature," Skeggs asserts.
If you have a WaitList.dat file on your system and peer inside you can find all sorts of potentially risky information. Of course to get to this file an 'attacker' would need to have access to your system somehow, directly or remotely. In WaitList.dat you could easily find passwords and other sensitive security info you might have typed into an email or document in the past. Notably, even if you delete a document its keystrokes may be saved in WaitList.dat. "On my PC, and in my many test cases, WaitList.dat contained a text extract of every document or email file on the system, even if the source file had since been deleted," Skeggs told ZDNet.

Apparently this file has been well known to DFIR and infosec experts since 2016 but recently Skeggs highlighted in a Tweet how an attacker quickly could grab just this one file to potentially reveal lots of user data in one swoop. WaitList.dat is a very juicy target and may be much quicker / easier to swipe than browser databases or password manager vaults.
Despite the above, Skeggs recognises WaitList.dat as a feature rather than a bug or vulnerability. If you want to check if you have this file on your PC it is usually stored at C:\Users\%UserName%\AppData\Local\Microsoft\InputPersonalization\TextHarvester\ and called 'WaitList.dat'.
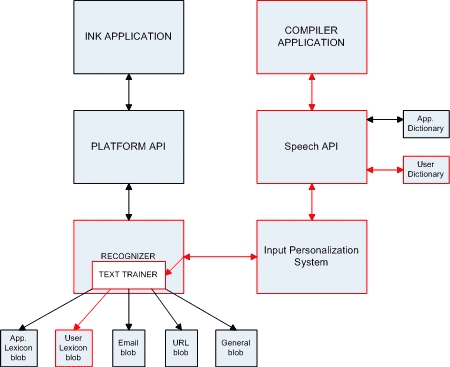
Representation of the relationship between Ink Applications and the IPS
I've checked my PC and found I do indeed have a WaitList.dat file that weighs in at 1.29MB. If that's pure text it could contain a lot of data. I've not had time to look through my WaitList file yet and I have a standard desktop PC without a stylus so am not sure why this was activated on my system. It might be due to the Traditional Chinese text input method installed as an alternative keyboard.
To disable the feature you can head on over to Windows Services and scroll down to 'Touch Keyboard and Handwriting Panel Service'. Right click to stop the service (if it is enabled).













