There is a security issue with Skype that is so problematic that it will require a major rewrite of the app, reports ZDNet. Microsoft has known about the bug, since at least September, and can reproduce the issue. However fixes will be delivered in a new version of the Skype client rather than an update as it is "too much work," to complete the bug fix now, says the source. While we wait, the bug could be exploited to escalate "a local unprivileged user to the full 'system' level rights - granting them access to every corner of the operating system".
Behind the security issue is an exploit technique called 'DLL hijacking'. Here's how it is possible:
- An attacker downloads a malicious DLL into a user-accessible temporary folder
- The attacker renames the DLL to one that can be modified by an unprivileged user, like UXTheme.dll
- The malicious DLL is found first when the Skype updater app searches for the DLL it needs during update
ZDNet explains that Skype has its own built-in updater and when it runs it uses another executable file to run the update, which is vulnerable to the hijacking.
While the attack is described as "on the clunky side," it could nevertheless easily be weaponised, insists Security Researcher Stefan Kanthak. For examples Kanthak supplied two command line examples, how a script or malware could remotely transfer a malicious DLL into that temporary folder. He went on to remind the reporter that DLL hijacking isn't limited to Windows systems, Macs and Linux systems are vulnerable too.
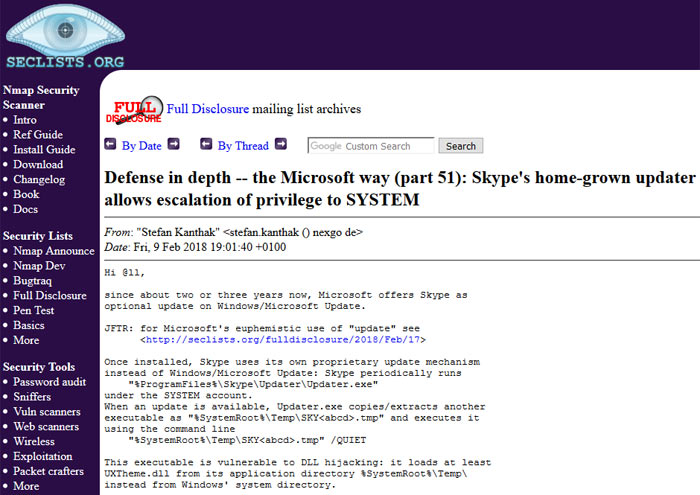
If exploited successfully the bug is rather serious. With 'system' privileges gained, an attacker "can do anything," Kanthak said. However Microsoft isn't rushing to fix this, as mentioned in the intro. Microsoft does say that it has put "all resources" into building an altogether new client. Remember this is a potential threat from local unprivileged users - not unknown remote hackers.













