Stick to the script
Google has changed the way it's Chrome browser handles insecure scripts on secure websites in Chrome 14, blocking them by default and leaving it up to users to enable them if needed. The goal is to impede cross-site scripting attacks that rely on the browser running the script before the user is away it is not safe to do so.
While many websites supply insecure scripts entirely innocently, it is also possible for malicious scripts to access content on an otherwise secure, which they shouldn't be able to. Unlike the display of static content on secure sites - such as images ad video - scripts have the potential to actively interact with a secure page, and are as such a greater threat to the secure browsing that HTTPS is intended to provide.
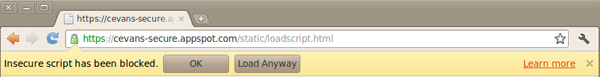
Previously Google Chrome indicated insecure scripts with a red strikethrough on the HTTPS icon in the location bar, and other browsers use a similar technique. However, the problem with this method of protection is that although users are made aware of the presence of insecure JavaScript, they are only notified after the script has already run. Obviously this isn't ideal as by the time users aware made aware there is a potential problem, the damage is already done. The new protected-by-default, conversely, requires that users opt-in to potentially dangerous JavaScript, hopefully reducing the instance of attacks of this nature.
Chrome 14 is currently only available in the browser's dev and 'canary' builds, so it won't hit all users for a while yet. Nonetheless, site developers who currently use insecure JavaScript and with a large base of chrome users will likely want to move to fix the 'issue' before the launch, lest they worry their visitors unduly once the update hits the main Chrome branch.













