Security
There are billions of mobile devices in the wild and almost all are connected to the Internet, with the promise of billions and billions more as the Internet of Things (IoT) takes shape. One obvious takeaway from such proliferation is that magnitudes more data will be produced around the globe, with the job of sifting through the proverbial chaff falling on the shoulder of big-data analytics.
Another, more worrying aspect of so many devices connected to the Internet and with so many services up in the cloud - banking, passwords, personal details, et al - is that hacking will become more pervasive. There are already countless stories of websites being hacked and personal and financial data being stolen. Digital security, therefore, is understandably a very hot topic.
Whose responsibility is security? Is it down to the hardware designer, the handset maker, the Internet service provider, or the application users connect to. One could argue that everyone is a stakeholder in Internet-related security.
As the dominant producer of the hardware architecture that powers most mobile devices and with new, related segments such as automotive and healthcare primed for expanding the overall reach, ARM is taking the responsibility for security very seriously.
As of 2017, ARM identifies security as one of the three pillars in building next-generation system-on-chip (SoC) processors, along with its expertise in low power and high performance. Security, it believes, needs to start at the very foundation of chip architecture, and has to be an equal partner to performance and efficiency.
Security is both a hardware and software problem, according to ARM, and it has a suite of technologies that serve to secure the popular Cortex range of processors. By providing a guiding light from inception, ARM helps a broad ecosystem of partners develop secure devices and applications.
For example, the latest ARM Cortex-M processors, primed for high energy efficiency in a cost-sensitive package, typically found in simple security products such as smartcards, now feature SecurCore technology for extra robustness.
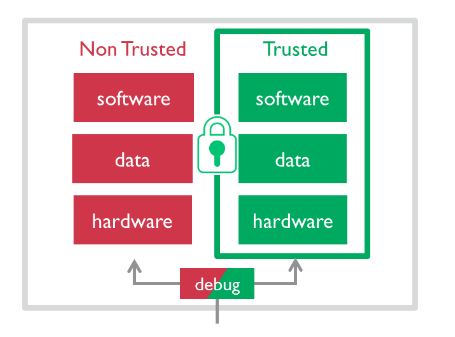
Moving on up the performance chain, ARM offers TrustZone CryptoCell embedded security platform where applications are launched in either normal or secure environments. In the latter scenario, non-secure software is blocked from accessing secure resources directly. Security is also enhanced at root by having data encrypted at source through industry-recognised standards such as AES and HASH.
ARM also guides software system architects on how to get the most out of TrustZone through software known as ARM Trusted Firmware. Available freely and able to be incorporated into leading operating systems, ARM also produces reference manuals and training software for easier implementation.
Security is very much a platform- and SOC-wide concern in ARM's eyes. Security is baked in on the initial design and hardware level, with the emphasis on the ecosystem to adopt a best-practice approach. Though it is everyone's concern, ARM is taking a leadership security position underscored by it supplying billions of chips into the Internet-connected ecosystem. Think mobile security, think ARM.