Features Overview - ActiveArmour and Networking
Remember the hardware network firewall in nForce3 250Gb, only available on that variant of the core logic? It's still around in nForce4, badged as ActiveArmour with enhanced performance, and firewall capabilities are offered on all nForce4 product variants.Firewall CPU offload
Most of the firewall's processing time is spent analysing packets flowing in both directions over the network interface. On a software firewall that's done entirely on the CPU, consuming CPU resources and processing time, reducing overall system performance. That's especially true when the data rate is high and you're using a hefty chunk of the available bandwidth.NVIDIA's ActiveArmour hardware can offload the analysis functions to the network controller, freeing up the CPU from that task. Things like checksumming (computing a value for that packet and checking it to make sure the integrity of the packet is correct and can be trusted) are all done on the network host. Even if the packet rate is high and you're using plenty of available network bandwidth, the CPU hit is zero to minimal, depending on the firewall settings.
You can also turn all the optimisations off if you want the CPU to handle the tasks, something that happens on certain variants of nForce4 by default. More on that later.
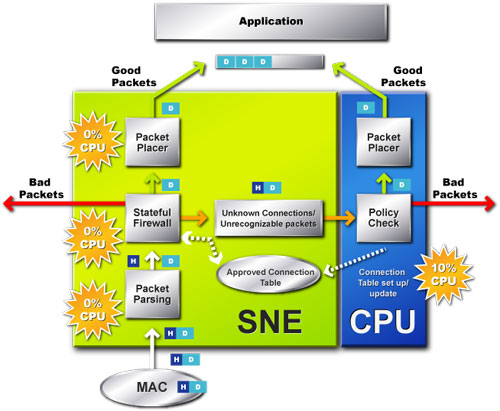
Firewall operation - NVIDIA supplied diagram
More user interaction
The new firewall software also is pro-active in interacting with the user when it has to. Alerts will popup near the system tray when an application the firewall isn't aware of tries to access the network, or when a connection is made to the interface from the network it's connected to. If the firewall is setup to prompt you, a simple dialog pops up and you can decide whether or not you want to allow that application or connection access out of, or into, your network interface.It remembers persistent settings if you tell it to. Say Doom3 wants to access the internet for you to play an online game. You allow that action the first time it asks you, choosing the Allow All option. Subsequent attempts by Doom3 to access the network are therefore granted by default. It's the same functionality available on all software firewalls, making an appearance in NVIDIA's software too.
Spoofing the system?
When an executable tries to access the outside network over the firewalled interface, the software records various parameters associated with the executable, including (but not limited to) name, size and date of creation. If you trust that executable, those parameters are added to a rules table that'll then allow that executable subsequent access to the outside network without it having to ask you. But what if a rogue executable, either spyware or a virus or worm, can spoof that information, taking on the exact size, name and other basic file attributes stored by the operating system? Will it be allowed access to the network, appearing as another application to the system?The short answer is no. The firewall software, when you first trust the application, computes a checksum for the executable. Now unless the executable trying to spoof the system has an identical checksum value to the trusted version, it'll be flagged as a spoof attempt and you'll be notified. Basically, unless the executables are identical (not just in size, but also in the data and how that data is laid out inside the binary itself), the checksums will be different.
The firewall software initially comes complete with a list of known, trusted executables and their checksums, so that basic software that requires internet access to function properly (things like your web brower, the Windows service host, some popular games binaries, popular IM clients and popular email clients) can do so without your intervention. You'll still be notified when the binary accesses the network interface, but it'll only be a notification and you'll be shown that the fireware software trusts that binary.
There's always human error to factor into a system like this, where you trust a bad binary without really knowing where it came from or why it needs a network connection, but the software does as much as it can to minimise that risk, with visual clues (the big red X is a handy hint) and hints as to what you should do for certain programs. As well as a trusted list of programs, the firewall also ships pre-loaded with checksum and file information for programs you absolutely should not trust, like the MSBlaster worm.
All of the above functionality comes under the Intelligent Application Manager umbrella.
Firewall basics
The firewall also does the basics, like only opening up ports as needed. As soon as an application doesn't need the port anymore, it's closed. You can also setup profiles for various modes of operation. Say you want to activate a profile that's a bit more secure than normal, when you're not at home behind your router and network connection that you trust, when you head off to a LAN party, you can do so in two clicks from a systray applet. Profile settings are numerous, but well explained (for the most part), so setting up user profiles is simple if you're prepared to read the documentation.Gigabit on all versions
All versions of nForce4 get Gigabit ethernet as standard and it now appears to be mandatory, along with the firewall, on all versions of nForce4. You'll see no dropping of the firewall or Gigabit capabilities on nForce4, even on the budget mainboards that implement it. That was maybe one of nForce3 250's biggest failings, that the basic and most attractive features of the core logic were often dropped by shipping mainboards as the Taiwanese manufacturers of the boards did their usual hyper-agressive cost-cutting across the board, especially on low-end budget boards. Even high-end boards would drop the firewall and use a completely separate LOM networking chip, utterly bypassing the network capabilities of nForce3 250. Infuriating!Hopefully that's not the case this time around and I'm somewhat assured on that fact by NVIDIA. Of course, the mass-market budget board vendors in Taiwan might just do what they like anyway, but here's hoping. Get the core features out to all customers buying nForce4-based systems and mainboards, please.









