You might have previously heard utterances, perhaps expletives, concerning BadUSB. It’s a Malware that reprograms USB chips in your devices with malicious intent. BadUSB is said to be able to bypass the OS, antivirus software and other countermeasures to do its dirty deeds. Your USB ports are particularly open to this kind of attack if you sometimes accept files, for example, provided on customer or colleague supplied USB sticks.
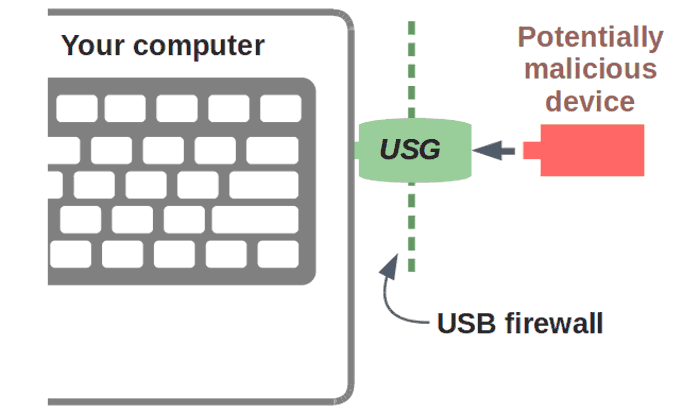
A couple of days ago Robert Fisk came up with a reasonable hardware solution to accessing untrusted USB devices. His 'USG' device is described simply as "a firewall for your USB ports". Unlike the drastic measure of disabling various exposed USB ports, or using a USB condom, the USG allows you to grab the data you need from that untrusted USB device that has been passed onto you.

New Zealand-based Fisk says that "The USG's firmware is fully open and auditable, so you can trust it. And when you use a USG, you no longer have to trust the opaque firmware of dubious origin running on every USB device you own." This device supports USB mass storage (flash drives), keyboards, and mice, with the possibility of other devices being added in the future.
The USG is completely plug and play and can be used with legacy and embedded systems with USB ports, as well as modern Windows, Mac OS, and Linux machines. Currently the USG has a couple of drawbacks; you can't connect a hub to it, and v1 of the USB uses 12Mbps hardware.
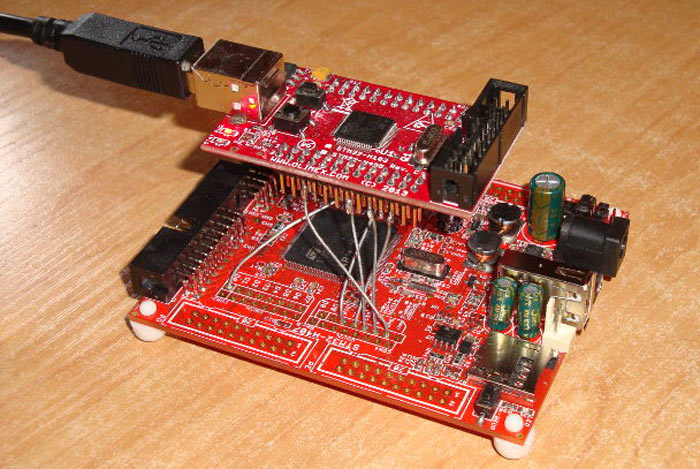
Robert Fisk is selling the USG v1.0 drives (pictured above) directly if you contact him. However in the spirit of open source hardware and software he also supplies links, instructions and diagrams so you can build your own v0.9 device (pictured below, costing about $50). It is even noted that "the truly paranoid" can build their own USG firmware.
If you are interested about the technical background, functionality, and use, of the USG there's plenty more to read on the source pages.













