In an email to HEXUS, and an associated blog post, Intel has announced that it has updated the microcode for all of the products it has launched in the past five years. Of course, it is talking about the CPU product range and their mitigations against the Meltdown and Spectre vulnerabilities. It may seem like this work has taken an eternity, but it has only been 74 days since the vulnerabilities came to light outside of a tight circle of security researchers and chip makers.
Intel CEO Brian Krzanich wrote that there have been thousands of people working tirelessly to protect customers and their data as per the Security-First Pledge he made in January. Furthermore, as per the pledge, a great deal of security work will go on.
The key part of the latest statement is that microcode updates for 100 per cent of Intel products launched in the past five years (those that require protection against the side-channel method vulnerabilities discovered by Google), have now been released. Krzanich took the opportunity to recommend that users don't just update their systems with these latest microcode patches but just generally keep their systems up to date as "It’s one of the easiest ways to stay protected."
With regard to Variant 1 (Spectre): CVE-2017-5753, Variant 2 (Spectre): CVE-2017-5715, and Variant 3 (Meltdown): CVE-2017-5754 - it is noted that Variant 1 will continue to be addressed via software mitigations, but Intel is making changes to its hardware design to further address the other two.
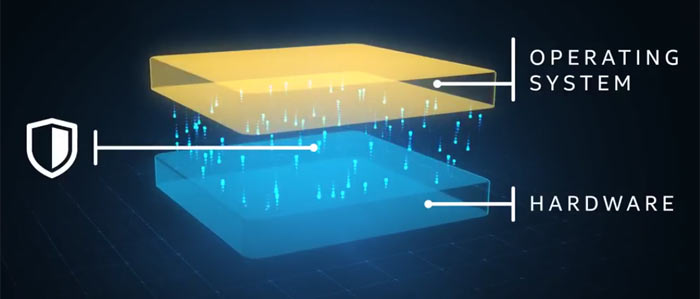
Hardware redesign
Intel notes that in-silicon fixes for Meltdown and Spectre will be baked into next-generation Intel Xeon Scalable processors (code-named Cascade Lake) and new 8th generation Core processors, expected to start shipping from H2 this year. The major change is described as the implementation of partitioning (simply visualised above). In effect this creates additional 'protective walls' between applications and user privilege levels to create an obstacle for bad actors, says Intel.













