Israel-based cyber-security research firm and consultancy, CTS Labs, today published a press release and other materials concerning multiple critical security vulnerabilities in AMD's 'Zen' core processor family. The firm issued its 'Severe Security Advisory' for AMD processors, backed up with a dedicated microsite called amdflaws.com, and an explainer video to sum up the reported issues and their scope.
According to CTS Labs there are thirteen critical security vulnerabilities and manufacturer backdoors distributed throughout the AMD Ryzen & EPYC product line. Yes, Ryzen Workstation, Ryzen Mobile, Ryzen Pro, and EPYC server processors all fall foul of one or more of the flaws discovered. The 13 serious flaws have been sorted into four categories by CTS Labs. A chart makes it very clear what processors are affected by what class of vulnerability, see below.
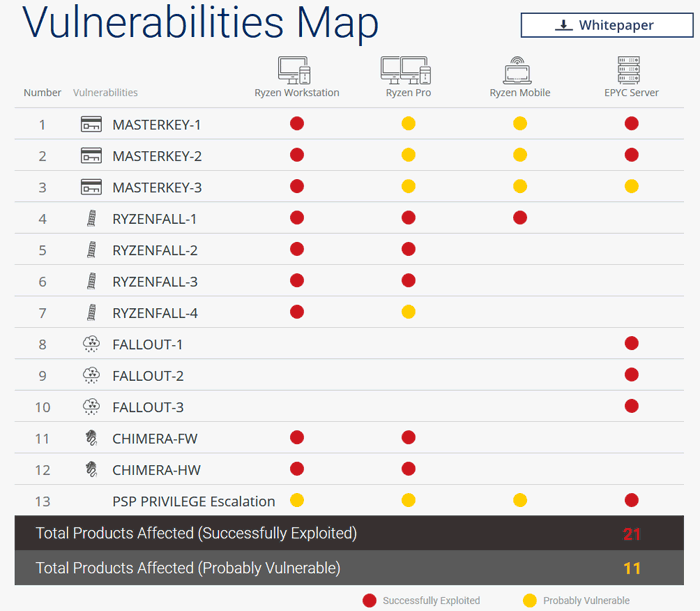
Three of four vulnerability classes require local admin access
Below I have shared key descriptive points concerning the four classes of flaws with notes on the prerequisites for exploitation. You will notice that three of the four vulnerability classes can only be taken advantage of if an admin runs some malware on the local system. Only Masterkey can be exploited initially as part of a remote cyber-attack, thinks CTS Labs.
- Masterkey (x3) vulnerabilities allow attackers to infiltrate the Secure Processor due to multiple vulnerabilities in the firmware. Exploiting MASTERKEY requires an attacker to be able to re-flash the BIOS with a specially crafted BIOS update.
- Ryzenfall (x4) allows malicious code to take complete control over the AMD Secure Processor. Exploitation requires that an attacker be able to run a program with local-machine elevated administrator privileges.
- Fallout (x3) allows attackers to read from and write to protected memory areas, such as SMRAM and Windows Credential Guard isolated memory (VTL-1). Exploitation requires that an attacker be able to run a program with local-machine elevated administrator privileges
- Chimera (x2) consists of two sets of manufacturer backdoors; one in firmware and another in hardware. Malicious code can be injected via these backdoors. Prerequisites for Exploitation are: a program running with local-machine elevated administrator privileges. Access to the device is provided by a driver that is digitally signed by the vendor.
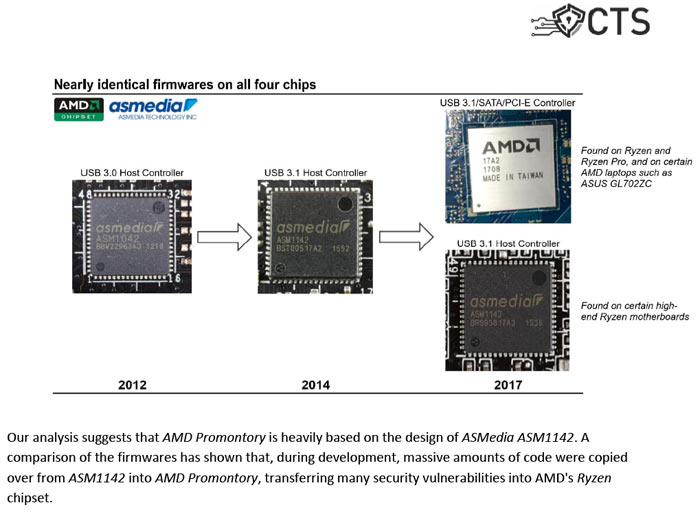
"Third-Party Chip Design Plagued with Hidden Backdoors" - root cause of Chimera flaws.
Unlike the other flaws, CTS Labs says that Chimera cannot be fixed by vendor updates and requires a workaround to prevent it potentially being exploited. CTS has already notified AMD and partners like Microsoft, HP, Dell, and ASMedia - plus select security companies - so that they can work on patches and mitigations. "To ensure public safety, all technical details that could be used to reproduce the vulnerabilities have been redacted" from the CTS Labs White Paper (PDF) which provides the greatest detail depth about the vulnerabilities.

I expect to get several emails from AMD and various security firms overnight. At the time of writing I think everyone is still digesting the dedicated amdflaws site and the white paper. Due to the limited possibilities of these vulnerabilities being exploited remotely and no evidence of associated malware in the wild one shouldn't worry too much at this time. Looking at AMD's share price, as I write, it is actually 1.8 per cent up on the day so far. It looks like this news caused a rather sharp downturn around 10.30am US time (news published at 10am US time), but it has more than recovered now.
UPDATE: AMD Responds
In a brief official statement on its investor relations page AMD has promised further updates on related security matters in the follow up to the CTS Labs news release.
"We have just received a report from a company called CTS Labs claiming there are potential security vulnerabilities related to certain of our processors. We are actively investigating and analyzing its findings. This company was previously unknown to AMD and we find it unusual for a security firm to publish its research to the press without providing a reasonable amount of time for the company to investigate and address its findings. At AMD, security is a top priority and we are continually working to ensure the safety of our users as potential new risks arise. We will update this blog as news develops."













