A significant redesign of the Windows, MacOS, and Linux kernels is needed to patch up an Intel processor security flaw. Modern Intel processors from the past decade are affected by the flaw. Exact details of the flaw is under wraps for now to give OS vendors time to patch, however it is thought that the code changes will have a significant impact on processor performance. The kernel changes could slow computers by between 5 and 30 per cent, depending upon task and processor model, reports The Register.
According to the source report the Intel x86-64 hardware flaw is such that kit cannot by fixed with a microcode update. "It has to be fixed in software at the OS level, or go buy a new processor without the design blunder," explains The Register. For Windows users it is expected that a patch is likely to be delivered for Patch Tuesday next week. Linux users have patches available but comments in the source code have been redacted so hackers don't have any insight into the issue.
Nature of the flaw
The flaw "allows normal user programs – from database applications to JavaScript in web browsers – to discern to some extent the layout or contents of protected kernel memory areas," according to the source. If hackers had a good grasp of this flaw now they would be able to make malware to read the contents of kernel memory which may contain hidden keys, passwords, caches and so on.
To patch this behaviour the kernel will have to be implemented with memory completely separated from user processes using KPTI, or Kernel Page Table Isolation. The separation will be impactful in the time taken by processes switching between two separate address spaces for every system call and hardware interrupt.
AMD processors don't have the KPTI flaw
"AMD processors are not subject to the types of attacks that the kernel page table isolation feature protects against," wrote Thomas Lendacky, a member of AMD's Linux OS group over the Xmas period. "The AMD microarchitecture does not allow memory references, including speculative references, that access higher privileged data when running in a lesser privileged mode when that access would result in a page fault."
It will be interesting to find out the impact of the OS-level patch for Windows / Intel systems on the tasks important to HEXUS readers. Hopefully any practical impacts will be in the lower percentage range.
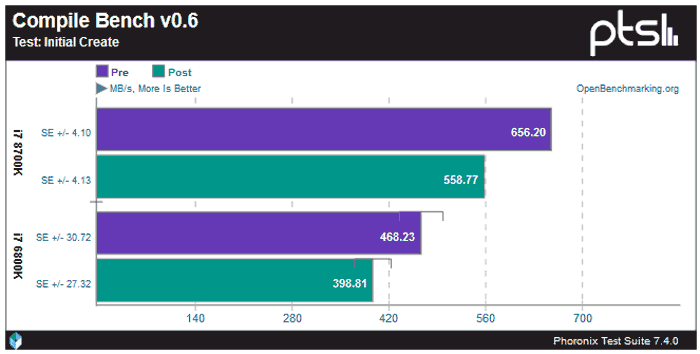
Linux specialist tech site Phoronix has already done some comparison testing on a Core i7-8700K processor and you can leaf through their set of results here. Some tasks are significantly impacted (one example shown above). However Linux gaming performance seems to remain unaffected by the patch.
Images from Phoronix.
UPDATE:
Intel has officially responded to today's security flaw reports in an email to HEXUS and via its official Newsroom Blog. In a nutshell it has issued a denial of sorts, saying that any exploits via flaws are not unique to Intel products. It then mentions how it is working closely with the likes of AMD, ARM Holdings and several operating system vendors to solve the issues discussed in the news above. Below is an excerpt of the statement for your convenience, or you can digest the full Intel blog post at the link above.
"Intel and other technology companies have been made aware of new security research describing software analysis methods that, when used for malicious purposes, have the potential to improperly gather sensitive data from computing devices that are operating as designed. Intel believes these exploits do not have the potential to corrupt, modify or delete data.
Recent reports that these exploits are caused by a “bug” or a “flaw” and are unique to Intel products are incorrect. Based on the analysis to date, many types of computing devices — with many different vendors’ processors and operating systems — are susceptible to these exploits.
-Snip-
Intel believes its products are the most secure in the world and that, with the support of its partners, the current solutions to this issue provide the best possible security for its customers".













