Unfortunately ransomware looks to have been a growing malware trend this past year. HEXUS doesn't follow the computer security scene very closely, as we are more focused upon hardware than software, but we have at least two stories in 2016 with ransomware; the first such malware to hit the Mac arrived in March, then a drive-by ransomware infection was infecting Adobe Flash users in April.

It's probably safe to say most malware writers and distributors have £$£$s in mind. Ransomware infections are very direct in their method of getting cash from victims. The malware will encrypt your documents. Then victims are asked for a payment to provide access to unlock these files. If they don't pay up to decrypt them, then the files will in effect be lost, unless there are some good recent data backups in place. If the malware afflicted user is lucky, one of the security application companies will publish a free de-encryption app targeting the malware that encrypted the files.
Popcorn Time 'refer a friend'
Over the weekend some new Windows malware called 'Popcorn Time' was highlighted by ZDNet. This ransomware innovated with a new kind of 'refer a friend' payment method, alongside the traditional demand for direct payment.
Popcorn Time encrypts your Documents, Pictures, Music and Desktop folders and files with a strong AES-256 encryption algorithm (it will also target files with 'media extensions' located elsewhere). What is an infected user to do? A payment of one bitcoin (approx $780, £618) will provide a key to unlock your files. However, there is a sinister alternative: if you share the malware with at least two other folk, who fall victim to it and 'pay up', then you can have a free decryption key.
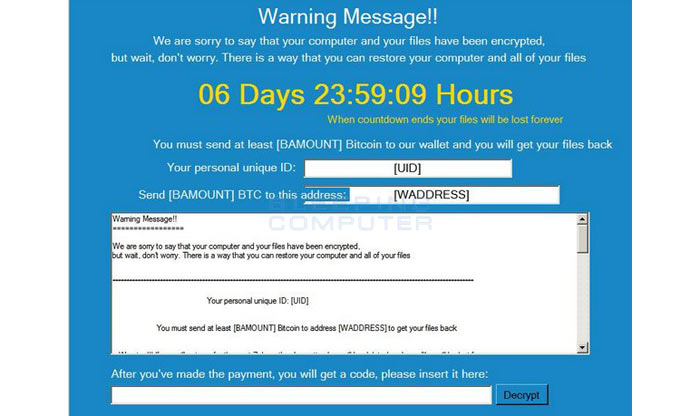
There are a couple of other interesting findings regarding Popcorn Time; firstly if a decryption code is entered incorrectly over a certain number of files then they will be permanently locked says ZDNet, secondly the criminals behind the ransom claim to be "extremely sorry" and will be using the money for "food, medicine, and shelter to those in need," in Syria.
According to Bleeping Computer, this Popcorn Time malware is not related to the Popcorn Time app for streaming copyrighted movies.













